Introduction
FTK Imager, an important tool in digital forensics developed by AccessData, operates similar to a meticulously preserved time capsule for the digital space. It stands out for its comprehensive approach to capture and preserve the state of storage devices.
FTK Imager goes beyond simple file copies, delving deep into the sectors of a device to capture every byte, including deleted fragments and hidden system information. It employs sophisticated hashing algorithms to ensure the integrity of the captured data, acting as a digital fingerprint for tamper-proof evidence. This versatile tool not only creates static snapshots but facilitates in-depth analysis, enabling investigators to uncover hidden secrets and bring justice to the digital world.
Features of FTK Imager 4.7.1
FTK Imager enables free and forensically sound full disk imaging for Windows, Linux, and various storage media.
Users can create custom content images, selectively choosing data to optimize investigative efficiency.
It supports read-only views through image mounting in Windows File Explorer.
It helps to generate hash reports (MD5, SHA-1) to verify the integrity of evidence.
It allows previewing forensic image contents across different storage media.
FTK Imager supports common forensic image formats for compatibility.
It also features RAM capture for live memory or registry analysis in digital forensics.
Installation
Go to the website: https://www.exterro.com/
Click on “Products” and then “FTK Imager”.

Click on “Download FTK Imager Now”.
Fill out all the details to download the latest version of FTK Imager.

Once the form is filled out the .exe file will be downloaded automatically.
Open File Explorer and execute the AccessData_FTK_Imager.exe file.
Follow the Installation Wizard and keep the default installation options (you can change the path and other settings if you need to).

Previews of Key Features:
Create Custom Content/Disk Images:
There are 5 options to choose from to create a forensic image:

Physical Drive - Captures entire storage device, including deleted files and unused sector, this is ideal for comprehensive forensic analysis.
Logical Drive - Captures data within a specific partition in a fast and compact manner, this is suitable for general backup.
Image File - Choose an image file as the source, for example, if you need to convert you forensic image from one format to another
Contents of a Folder - Selective copy of a directory or subdirectory, suitable for targeted backup and archiving without any deleted files.
Fernico Device (multiple CD/DVD) - Restore images from multiple CD/DVD
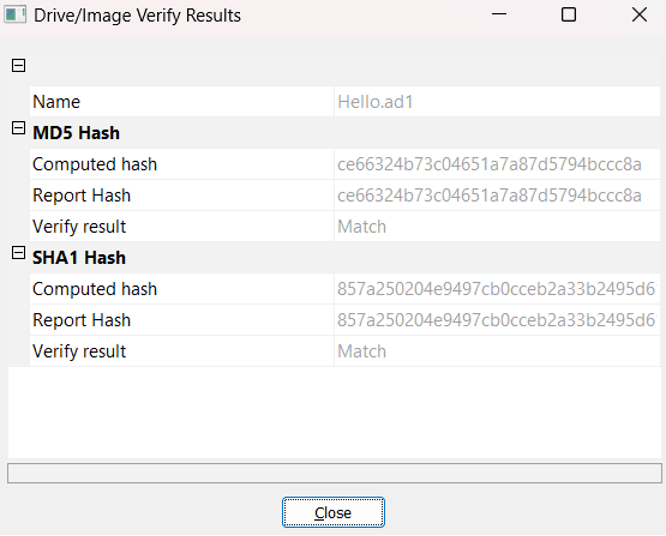
Hash Reports
When creating an image, you can select the option of "Verify images after they are created". This will check if the integrity between the initial data and the captured data.
Summary
FTK Imager is like your digital Sherlock for preserving evidence, it captures every byte of storage devices including deleted traces. It offers free forensic imaging, selective captures, integrity checks, and even memory analysis – all to help uncover hidden truths and protect digital evidence.
Download and start your digital investigation journey today!🕵️♂️🔍✨

